How to configure an access control system?
Do you know how to configure access control system?And what parts does an access control system have?
1,485 bus network access control system configuration principles and methods
1.1 Card reader and button configuration principles:
In principle, one door with one door reader and one exit button.If the customer requests to choose a good cost-effective ID card, please choose the ID card reader, if the customer for consumer and other card occasions, please use Mifare IC card reader.
If the customer requests to go out to swipe credit card verification, then a door configuration two card reader, no need exit button.
If the customer requests to go out to swipe credit card verification, then a door configuration two card reader, no need exit button.
Note: In some special occasions, for example, the company needs to install an exit button to go out the door and the front desk, the door needs to be configured with two buttons, and the exit button of the same door can be used in parallel.
1.2 The controller configuration principles:
There are several doors in a local area to configure the number of controllers. For example, a small area (which can be routed and the distance between the card reader and the controller installed is less than 100 meters) has 3 doors and a single door controller and a 2-door controller is selected.
The controller has single-door two-way,2-door two way and four-door one-way. The so-called two-way is that you can access the door out of two readers, you can also access a card reader and a go button. One way is to access the door then card reader, go out the door button must be connected. Therefore, if there are four doors in one area that require access to both cards, you can not allocate four controllers. You need to configure two two-door and two-way controllers for the four doors.
1.3 As many controllers as you need, as many chassis and power supply you need.
1.4 232 / 485 communication converter configuration principles:
If the total number of access control system controller does not exceed 80, in principle, only one 485 converters are required.
Note: If the entire access control system has only one controller, and the controller position can be placed next to the control computer, the card reader lock to the controller connection distance of fewer than 100 meters, then no need to configure the 485 converter with The original controller 232 serial data cable to the computer and the controller can be connected to the communication.
Note: The computer is connected to the 485 converters, the 485 converters is connected to the first controller, and the first controller is connected to the second controller, so that it goes hand in hand, and the farthest controller connects to the 485 converters Proposed within 800 meters from the distance, if more than 800 meters, please add a 485 extension repeater.
1.5 The configuration principle of electric lock:
In principle, one door has one magnetic lock. The company's door is double open glass doors, generally about two doors with an electric bolt lock.
Glassdoor should choose electric bolt lock, wooden doors and fire doors should choose the magnetic lock (electromagnetic lock), there are customers pay attention to safety and aesthetics of the choice of electric plug.
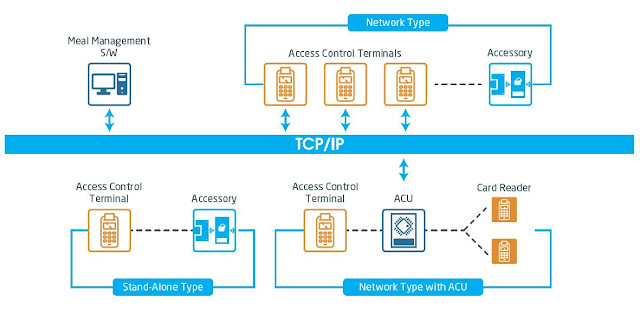
2, TCP / IP network LAN access control system configuration principles
2.1 Configuration method, basic and 485 bus access control system configuration method is the same. The following points are different.
2.1 Configuration method, basic and 485 bus access control system configuration method is the same. The following points are different.
2.2 Without 485 converters, HUB (or switch) can be used to choose the original customer's LAN or purchased, any local area network can use HUB (or switch) can be.
2.3 Wiring and LAN computer wiring, as required to the controller to the HUB distance of fewer than 100 meters, it is recommended within 80 meters, and the quality of network cable should not be too bad. As long as cascaded down through the HUB, the total number of systems is unlimited.
3, TCP / IP Internet access control system configuration principles and methods
Configuration method, basic and TCP / IP LAN access control system configuration method. The following points are different.
Configuration method, basic and TCP / IP LAN access control system configuration method. The following points are different.
Each region needs to be shared by a designated model of router to the Internet. (Note: Why specify the model? Specified models in the corresponding program, because our manual is prepared according to this model, some routers do not have this feature, we specify the router's brand price and quality are good, you can To the local electronic computer market to buy this router can be with the client's computer Internet access, without special.)
4, Case:
For example, 20 doors 485 networking access control system project, one gate is a double open glass door and far away from other doors. A region has two wooden doors are more concentrated, a region has five single open glass door is more concentrated, a region There are 12 wooden doors more focused on such a scene of the access control system configuration.
For example, 20 doors 485 networking access control system project, one gate is a double open glass door and far away from other doors. A region has two wooden doors are more concentrated, a region has five single open glass door is more concentrated, a region There are 12 wooden doors more focused on such a scene of the access control system configuration.
- The gate uses a card reader. Because it is a double open glass door, it is recommended to pick two electric bolt locks.One single-door controller and one exit button.
- Two doors in one area: One double door controller, two door readers, two electromagnetic locks and two exit buttons.
- Five doors in one area: One single-door controller + one four-door controller, five-door readers and five exit buttons.
- An area of 12 doors. Adopt 3 four-door controllers, 12 door readers, 12 out buttons, 12 magnetic locks.
- In addition, a communications hub (485 converters) and a set of management software are required.
5, Unconventional other complex requirements of the configuration principles:
- If the customer asked not only to enter the door when the credit card, but also to enter the password, the password is correct before the passage of the door reader to use password keyboard reader.
- If the customer asked to pick the fingerprint device, without a card reader, use the fingerprint reader with wiegand26 international standard output interface instead of the corresponding card reader on it, 80% of the fingerprint device on the market with a wiegand26 standard output interface.
- If you need to fire the door to open the door illegally broke into the alarm door for a long time did not close the coercion alarm card alarm and other alarm functions, each controller needs to be equipped with alarm output and fire linkage expansion board.
For more information about access control system, please visit my "ShineACS Access Control Security" main website--It is a FREE website that you can download access control system knowledge and find right suitable access control products and solutions for your access control project.



Comments
Post a Comment